This page provides an overview of the products' evolutions deployed this month.
[New Feature] [CORE] Reports Lifecycle
Key changes
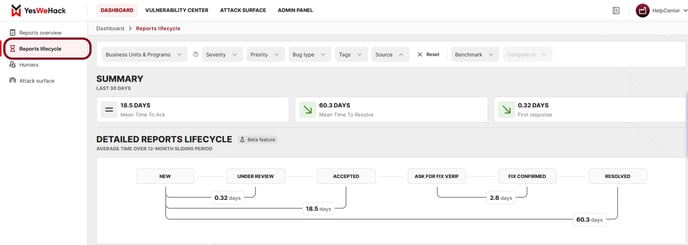
The dashboard now includes a new feature: “Reports Lifecycle.” This new page enables organisations to track key workflow metrics related to their reports and benchmark them against industries, their own other programs, other companies from their country, or even the overall platform average.
Impact
- The new dashboard empowers organisations to evaluate and clearly communicate their overall vulnerability management maturity.
- It also allows users to benchmark their performance against industry standards or peers, providing valuable insights into how effectively they are managing vulnerabilities.
- Comparison points at each step of the workflow help organisations identify specific areas to focus on and prioritise improvements.
Audience
- Program Managers looking for metrics that support both compliance and security operations. For instance “New to Resolve” (i.e., MTTR) reflects the full remediation workflow — not just activity within the YesWeHack platform.
- Program Managers assessing their program performance, with benchmark capabilities on indicators such as “New to Reward” — a critical factor for both program attractiveness and Hacker engagement.
Usage
- Users can access the Reports Lifecycle through a dedicated page on the Dashboard.
- Metrics are tracked over the past 12 months, enabling teams to monitor progress and identify trends over time.
Learn more about Reports Lifecycle here: https://helpcenter.yeswehack.io/reports-lifecycle-dashboard
---
[New Feature] [ASM] Toggle a Revamped Attack Surface Management Experience
Key changes
A brand-new user experience has been released for our Attack Surface Management (ASM) solution.
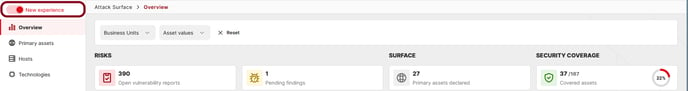
The Attack Surface Management page will contain 4 new tabs:
- Overview: Quickly assess your external exposure with key surface indicators, risk summaries, and asset coverage metrics. This view also highlights the Top 10 scopes requiring immediate attention, helping you prioritise where it matters most.
- Primary Assets: Get a comprehensive view of your assets and their current coverage. Deep dive on each assets to discover its underlying hosts and technologies.
- Hosts: Explore all the hosts across your assets. Pivot on this view to display the vulnerability reports & findings which involve these hosts, as well as services & technologies running on them. Seamlessly add your Hosts to Bug Bounty or Pentest program in a few clicks.
- Technologies: Gain visibility into the technologies and software components deployed on your stack to spot potentially vulnerable technologies across your assets.
Impact
- This redesign has been built to improve visibility and actionability across risks and assets.
- Revamping the UX is the first milestone in a series of upcoming improvements and feature launches on ASM. Stay tuned!
Audience
The new ASM UX has been designed to benefit every organisation by offering 3 distinct entry points into the same dataset:
- Primary Assets
- Hosts
- Technologies
These entry points allow users to explore and pivot based on their specific use cases and priorities. For example:
- CISOs wanting to have a high level picture of the organisation’s attack surface, risk, and where to focus (overview page).
- Program Managers reviewing their Primary Assets (e.g., through tags) to track their current coverage (Primary Assets page).
- Program Managers evaluating hosts to add them as scopes to Bug Bounty programs or Pentest campaigns (Hosts page).
- Program Managers assessing which hosts are impacted by a new CVE (Technologies page).
Usage
This preview phase will run for a few months before the new experience becomes the default.
- Toggle the new UX with a dedicated button at the top left corner.
---
[Improvement] [DOJO] OAuth implementation
Key changes
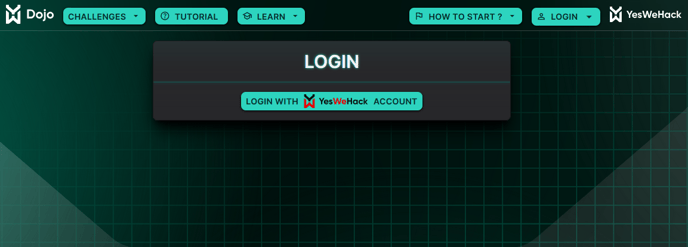
Users can now log in to the Dojo using their YesWeHack account directly instead of a separate authentication system.
Usage
- A new “Login with YesWeHack account” button is available on the Dojo login page
- Users already logged in the platform will automatically authenticate on the Dojo by clicking on this button
- Others will be redirected on the YesWeHack platform to authenticate
---
[Improvement] [MISC] Strong customer authentication (SCA)
Key changes
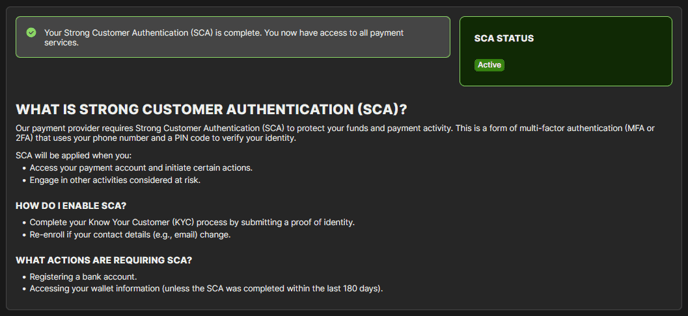
The YesWeHack payment provider requires Strong Customer Authentication (SCA) to protect your funds and payment activity. This is a form of multi-factor authentication (MFA or 2FA) that uses your phone number and a PIN code to verify your identity.
Impact
SCA will be applied when you:
- Access your payment account and initiate certain actions
- Engage in other activities considered at risk
Usage
Learn more about KYC & SCA with our dedicated HelpCenter article: https://helpcenter.yeswehack.io/kyc-verification-and-sca
---
[Improvement] [CORE] Triage Workflow
Key changes
We’ve introduced a new workflow designed to streamline your interactions with the triage team. This workflow complements the existing report process and aims to give you better visibility on the progress of triage operations.
This new workflow has been deployed automatically, without impacting your team members, and does not require any action on your side.
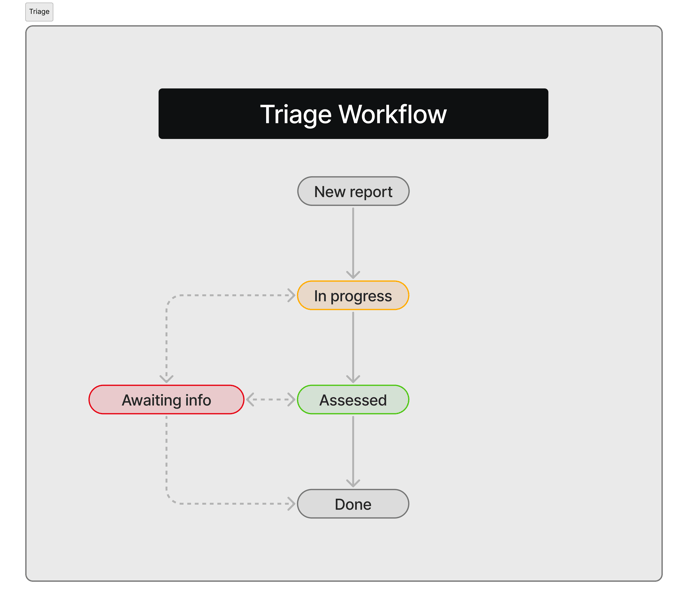
- Reports now include a new indicator showing the progress of the triage process.
- New targeted comment actions allow you to address messages specifically to Hunters, Triagers, or Team members.
- The assignment system will no longer be used by the triage team. Assignments will of course remain available for your own vulnerability management needs.
Impact
This new workflow introduces several changes to the platform:
- Additional Triage Progress Indicators – Clear visual markers to track report status.
- Comments & Assignments on Reports – The ability to post comments for specific audiences, including Team, Triage, and Hunters.
Usage
Learn more about this new triage workflow on our HelpCenter page: https://helpcenter.yeswehack.io/vulnerability-reports-workflow
